Last month, the Shanghai High Court released an interesting case. A car owner, after an accident with their electric vehicle, chose a regular auto repair shop due to the high cost and long wait time for factory repairs. The two brothers running the repair shop discovered that the vehicle’s battery management system had automatically locked the battery output power after the accident. They unlocked it by modifying the software data of the battery management system. Later, they attracted another customer online and performed the same unlocking service on another vehicle. In total, they charged 5,000 yuan for the repairs. As a result, the two brothers were sentenced by the Jiading District Court in Shanghai for the crime of damaging computer information systems.
The Verdict
After hearing the case, the Jiading District People’s Court ruled:
Da Liu and Xiao Liu, for illegal profit, violated national regulations by modifying the data stored, processed, or transmitted in the computer information system of a new energy vehicle. This led to distorted data collection for the vehicle’s battery operation, affecting the safety regulation of the new energy vehicle, with serious consequences. Their actions constituted the crime of damaging computer information systems. This case is a joint crime; both defendants truthfully confessed their crimes and voluntarily admitted guilt, which allows for a lighter punishment and lenient treatment. Considering the specific roles of the two defendants in the joint crime, the social harm of the case, and the full restitution of illegal gains, the court sentenced Da Liu to six months in prison, suspended for one year, and Xiao Liu to six months of detention, suspended for six months. The illegal gains and tools of the crime were confiscated.
The Crime of Damaging Computer Information Systems
In recent years, two of the most notorious crimes in the field of computer information are the Crime of Assisting Information Network Criminal Activities and the Crime of Damaging Computer Information Systems. The former has quickly become one of the most common charges in practice. According to a research report released by the Supreme People’s Court, from 2017 to 2021, there were 67,000 cases nationwide involving 143,700 people, with a rapid and continuous increase. The latter, however, involves only two to three hundred people annually.
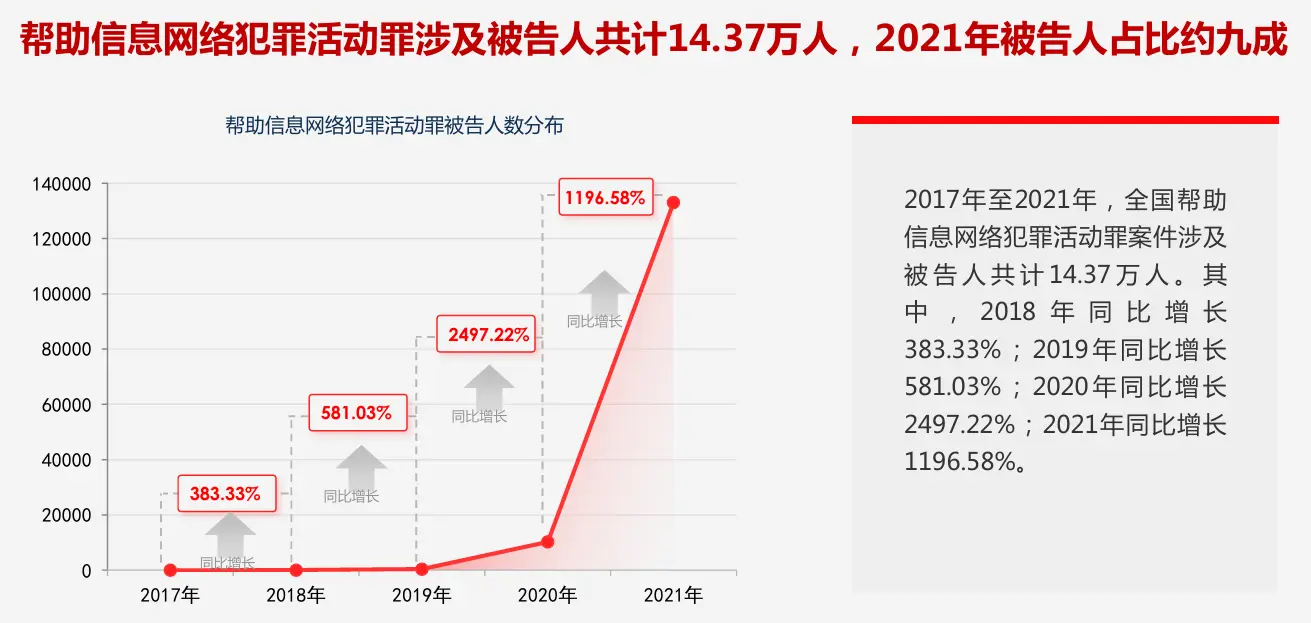
Why a Crime Involving Only Two to Three Hundred People Annually Attracts So Much Attention
The Crime of Damaging Computer Information Systems, being a relatively small-scale crime in practice, has garnered widespread attention mainly due to the vague wording of the criminal law itself. The focus should be on the specific scenarios listed in the judicial interpretations by the “Two Supremes” (the Supreme People’s Court and the Supreme People’s Procuratorate).
- Criminal Law
Article 286 [Crime of Damaging Computer Information Systems] Violating national regulations, deleting, modifying, adding, or interfering with the functions of a computer information system, causing the system to fail to operate normally, with serious consequences, shall be punished with up to five years of imprisonment or detention; if the consequences are particularly serious, the punishment shall be more than five years of imprisonment.
Violating national regulations, deleting, modifying, or adding data or applications stored, processed, or transmitted in a computer information system, with serious consequences, shall be punished according to the preceding paragraph.
Intentionally creating or spreading computer viruses or other destructive programs, affecting the normal operation of a computer system, with serious consequences, shall be punished according to the first paragraph.
If a unit commits any of the above crimes, the unit shall be fined, and the directly responsible persons and other directly responsible personnel shall be punished according to the first paragraph.
- Judicial Interpretation by the “Two Supremes” on Several Issues Concerning the Application of Law in Handling Criminal Cases Endangering Computer Information System Security
Article 4 Damaging the functions, data, or applications of a computer information system, under any of the following circumstances, shall be deemed as “serious consequences” as stipulated in the first and second paragraphs of Article 286 of the Criminal Law: (1) causing the main software or hardware of 10 or more computer information systems to fail to operate normally; (2) deleting, modifying, or adding data stored, processed, or transmitted in 20 or more computer information systems; (3) illegal gains of 5,000 yuan or more or causing economic losses of 10,000 yuan or more; (4) causing a computer information system providing basic services such as domain name resolution, identity authentication, or billing for 100 or more computer systems or serving 10,000 or more users to fail to operate normally for a cumulative period of one hour or more; (5) causing other serious consequences.
Committing the acts stipulated in the preceding paragraph, under any of the following circumstances, shall be deemed as “particularly serious consequences”: (1) the quantity or amount reaching five times the standards specified in items (1) to (3) of the preceding paragraph; (2) causing a computer information system providing basic services such as domain name resolution, identity authentication, or billing for 500 or more computer systems or serving 50,000 or more users to fail to operate normally for a cumulative period of one hour or more; (3) damaging the functions, data, or applications of a computer information system providing public services in fields such as state organs, finance, telecommunications, transportation, education, medical care, or energy, severely affecting production or life or causing adverse social impact; (4) causing other particularly serious consequences.
Article 6 Intentionally creating or spreading computer viruses or other destructive programs, affecting the normal operation of a computer system, under any of the following circumstances, shall be deemed as “serious consequences” as stipulated in the third paragraph of Article 286 of the Criminal Law: (1) creating, providing, or transmitting computer viruses or other destructive programs, causing the program to spread through networks, storage media, files, or other mediums; (2) causing 20 or more computer systems to be implanted with programs specified in items (2) and (3) of Article 5; (3) providing computer viruses or other destructive programs to 10 or more people; (4) illegal gains of 5,000 yuan or more or causing economic losses of 10,000 yuan or more; (5) causing other serious consequences.
Committing the acts stipulated in the preceding paragraph, under any of the following circumstances, shall be deemed as “particularly serious consequences”: (1) creating, providing, or transmitting programs specified in item (1) of Article 5, causing the program to spread through networks, storage media, files, or other mediums, severely affecting production or life or causing adverse social impact; (2) the quantity or amount reaching five times the standards specified in items (2) to (4) of the preceding paragraph; (3) causing other particularly serious consequences.
For example, in the Jiading case, the court clearly applied item (3) of Article 4 of the judicial interpretation, where the illegal gains of the two brothers reached 5,000 yuan.
Case Warning
If we only look at the criminal law text, “deleting, modifying, adding, or interfering with the functions of a computer information system, causing the system to fail to operate normally” is a broad and vague definition, making it difficult to interpret in practice.
Especially item (2) of Article 4 in the judicial interpretation: deleting, modifying, or adding data stored, processed, or transmitted in 20 or more computer information systems should be deemed as “serious consequences,” which can easily cause confusion for IT professionals. For example, during system maintenance, data cleaning, software updates, data backups, or debugging, if errors cause more than 20 computers in a company to fail to operate or result in a loss of more than 10,000 yuan, does it constitute a crime?
However, the criminal law generally follows the principle of “restraint.” To constitute a crime, there must first be a clear criminal intent, and the actions taken must be explicitly illegal under the law. The consequences, besides those stated in the legal text, should also have a certain degree of social harm. For instance, in the case of the two brothers modifying the battery data to unlock the vehicle, besides damaging the monitoring data of the electric vehicle manufacturer, it indeed increased potential social risks.
However, there are still some deficiencies in the legislation of this crime. The “violation of national regulations” mentioned in the criminal law lacks a comprehensive set of rules in reality. Some cases in practice refer to “national regulations” scattered in various administrative regulations and judicial interpretations, such as the judicial interpretation by the “Two Supremes” on several issues concerning the application of law in handling criminal cases of environmental pollution, which targets interference or data tampering with environmental quality monitoring systems, and the illegal acts listed in the Computer Information System Security Protection Regulations and the Railway Computer Information System Security Protection Measures.
As for whether the data monitoring methods of electric vehicle manufacturers are reasonable, that’s another matter. It can only be said that times are changing, and while new energy vehicle owners enjoy intelligent and connected services, they also have to pay a certain price.

