Security Settings for Using CloudFlare R2 as an Image Host to Prevent Malicious Class B File Requests

CloudFlare R2 is a groundbreaking free service generously offered by the good folks at Cloudflare, providing users with 10GB of storage and unlimited bandwidth by default. However, this "unlimited" comes with some restrictions: no more than 1 million write operations and 10 million read operations per month, beyond which usage will be billed accordingly. Recently, I migrated over 110,000 images to R2 and became concerned about exceeding these limits, so I implemented strict security measures.
Protection Principles
The R2 bucket I needed to secure is part of the soomal.cc website mentioned in the article Migrating Soomal.cc to Hugo
.
The website is already hosted on Cloudflare Pages, which provides free hosting. The focus here is securing the images referenced in the HTML.
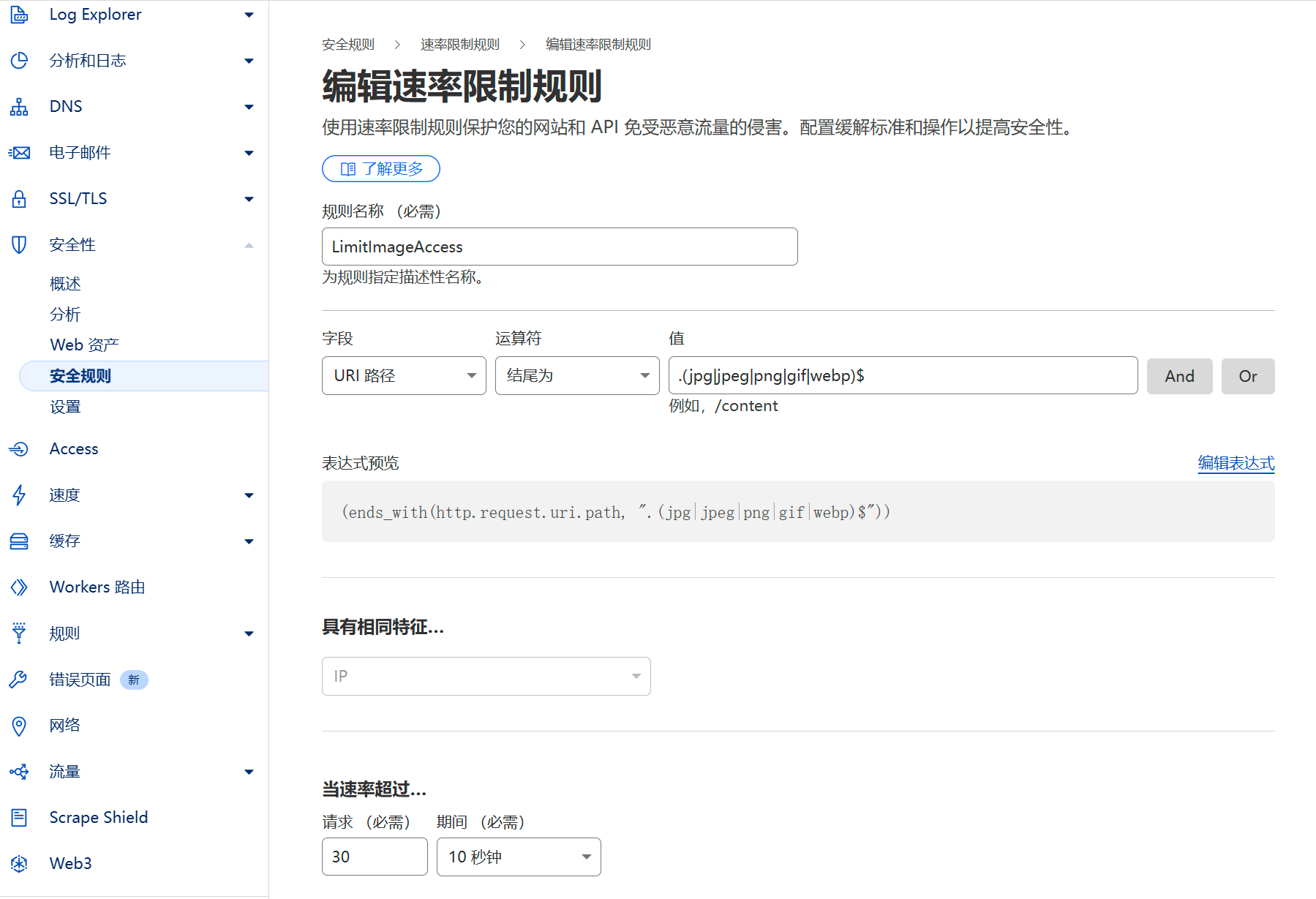
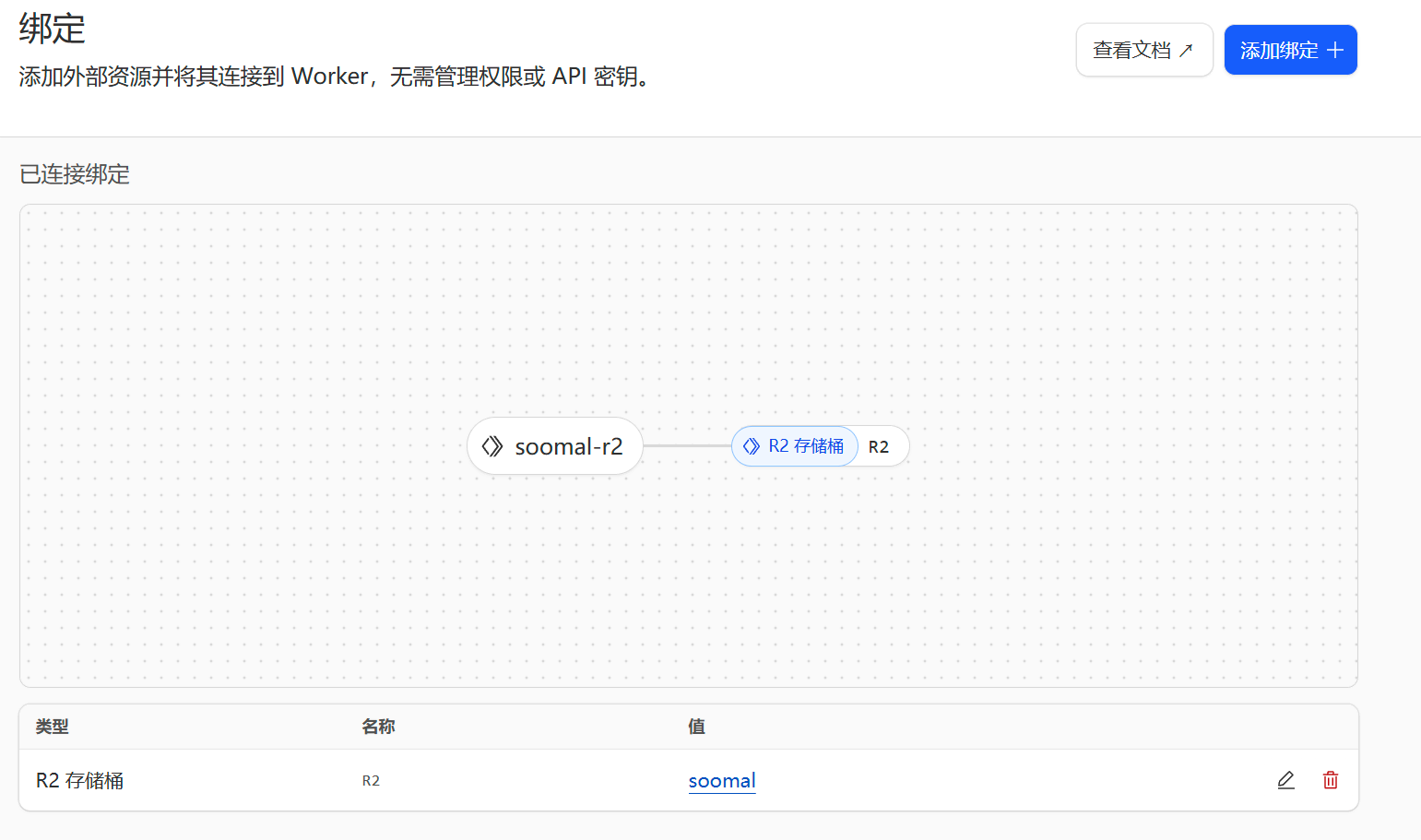
Restrict direct access to the R2 bucket. Prevent direct access to the R2 bucket via URLs, allowing access only through Cloudflare Workers.
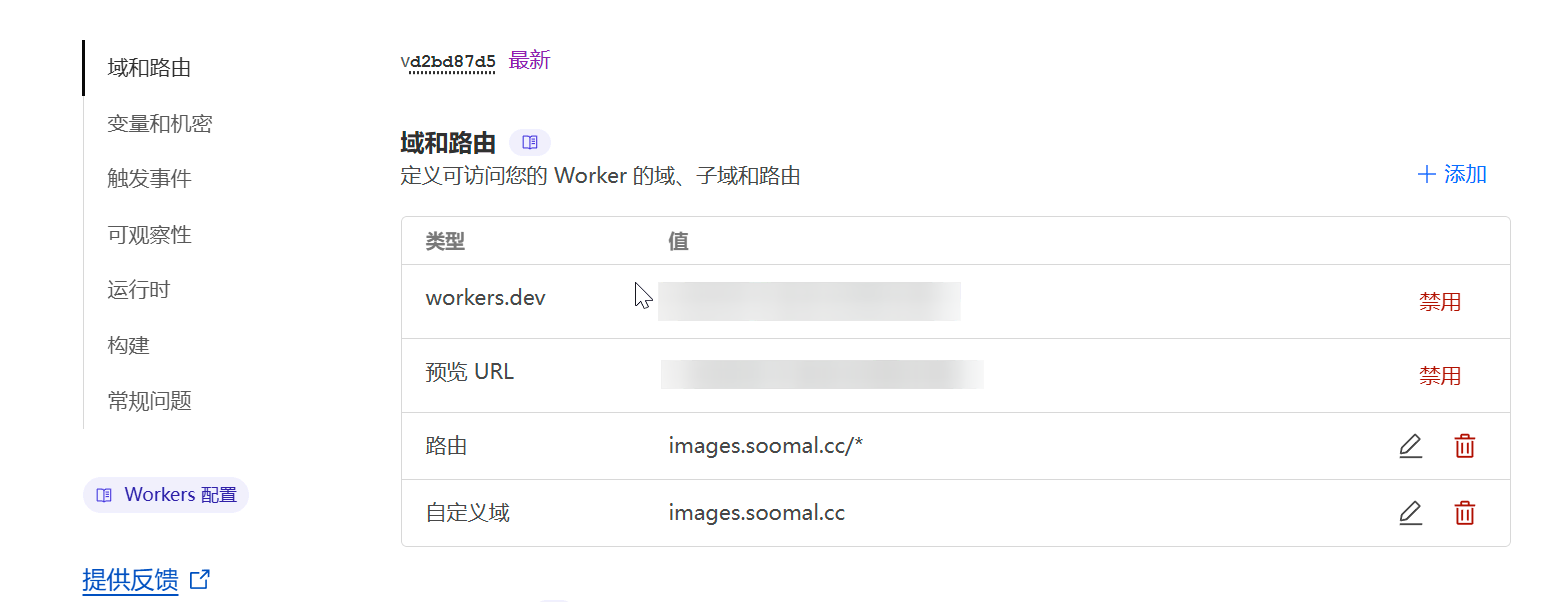
Restrict direct access to image URLs. Block direct requests to image URLs like
https://images.soomal.cc/test.webp, ensuring all image requests are made within the context of the original website.Implement appropriate security policies on the origin site. Since images themselves aren't suitable for overly restrictive rules, the main approach is to increase the difficulty of directly requesting image links by enforcing security measures on the origin site.
Configuration Steps
Disable R2 Public Access
In the R2 settings, avoid configuring custom domain access and do not expose R2 publicly on the web.
For CORS policies, restrict access to the origin site only.
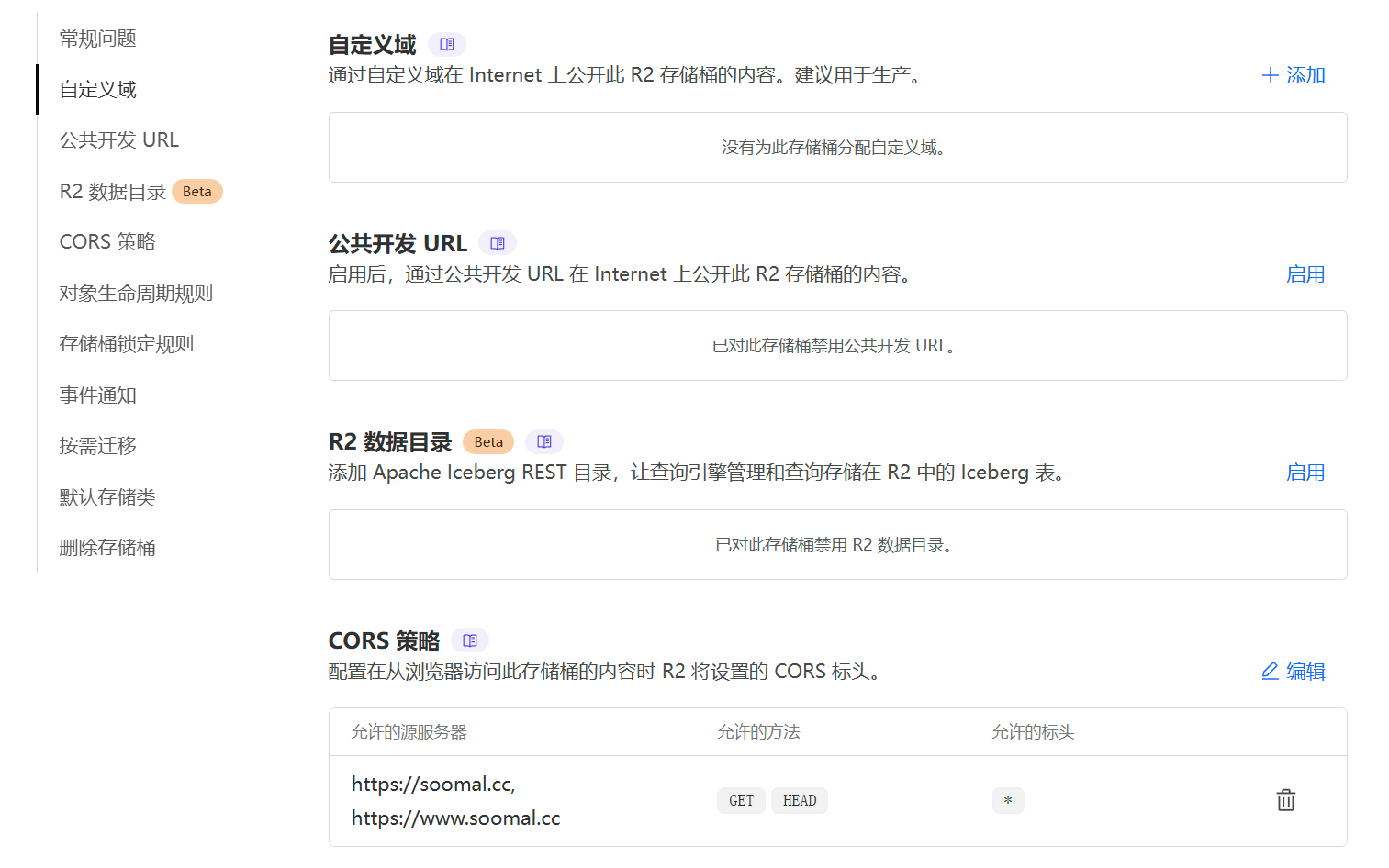
1[
2 {
3 "AllowedOrigins": [
4 "https://soomal.cc",
5 "https://www.soomal.cc"
6 ],
7 "AllowedMethods": [
8 "GET",
9 "HEAD"
10 ],
11 "AllowedHeaders": [
12 "*"
13 ],
14 "ExposeHeaders": [
15 "ETag"
16 ],
17 "MaxAgeSeconds": 3600
18 }
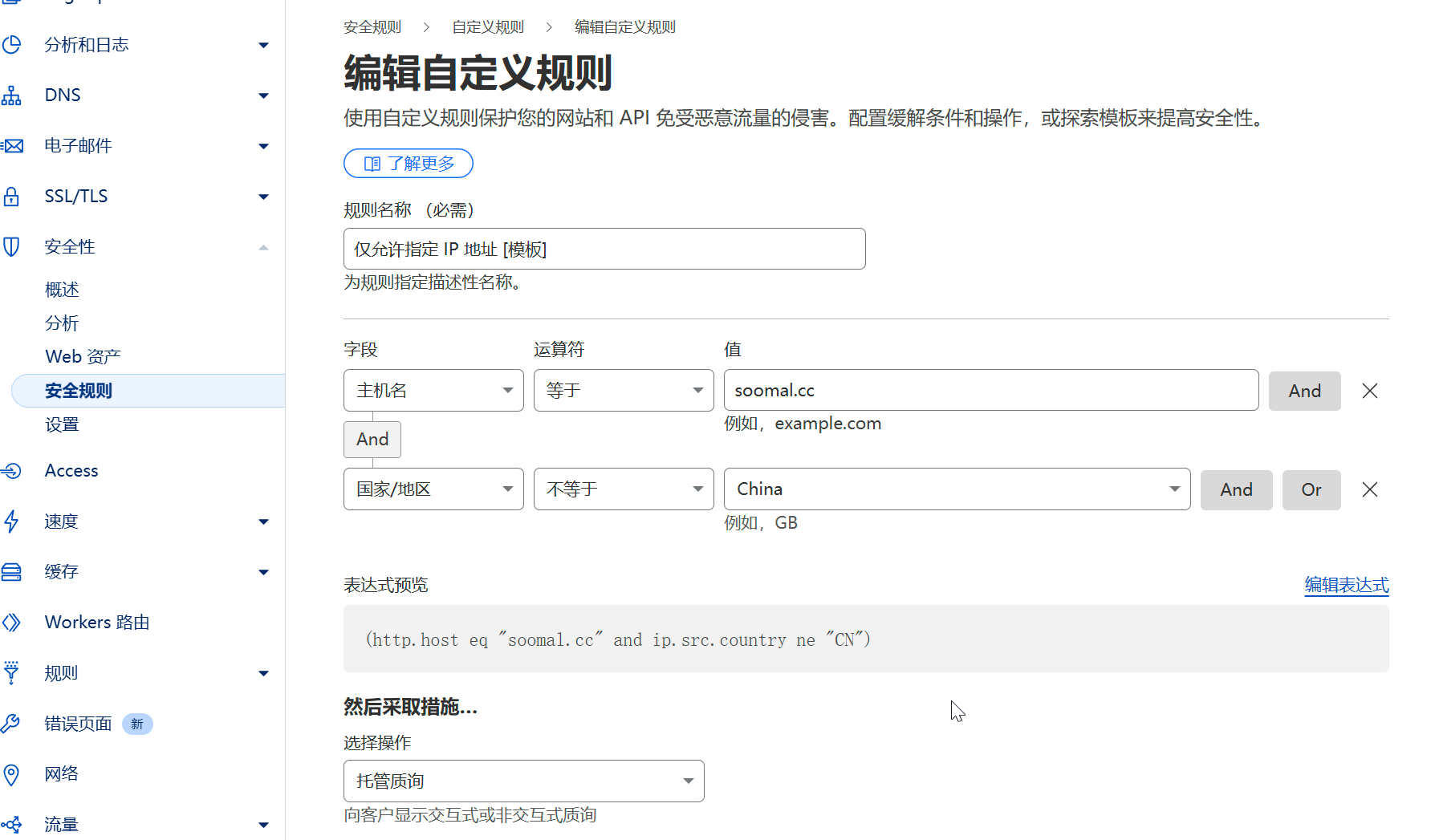
19] Add Workers Access Rules
- Create a Worker.
- Bind the R2 bucket.
- Add a custom domain and route.
- Add Worker script.
1addEventListener('fetch', event => {
2 event.respondWith(handleRequest(event.request));
3});
4
5async function handleRequest(request) {
6 const url = new URL(request.url);
7 const referer = request.headers.get('referer');
8 const allowedDomains = ['soomal.cc', 'www.soomal.cc'];
9
10 // Handle image requests for images.soomal.cc
11 if (url.host === 'images.soomal.cc') {
12 if (referer && allowedDomains.some(domain => referer.includes(domain))) {
13 const filePath = url.pathname.replace(/^\//, '');
14 try {
15 const object = await R2.get(filePath);
16 if (object === null) {
17 console.log(`File not found: ${filePath}`);
18 return new Response('File Not Found', {
19 status: 404,
20 headers: { 'Content-Type': 'text/plain' }
21 });
22 }
23 const headers = new Headers();
24 headers.set('Content-Type', object.httpMetadata.contentType || 'image/webp');
25 headers.set('Cache-Control', 'public, max-age=31536000');
26 headers.set('Access-Control-Allow-Origin', 'https://soomal.cc');
27 return new Response(object.body, { status: 200, headers });
28 } catch (error) {
29 console.log(`Error: ${error.message}`);
30 return new Response('Internal Server Error', {
31 status: 500,
32 headers: { 'Content-Type': 'text/plain' }
33 });
34 }
35 }
36
37 console.log(`Unauthorized: Referer ${referer} not allowed`);
38 return new Response('Unauthorized Access', {
39 status: 403,
40 headers: { 'Content-Type': 'text/plain', 'Cache-Control': 'no-store, no-cache' }
41 });
42 }
43
44 // Return 404 for requests not targeting images.soomal.cc or www.soomal.cc
45 return new Response('Not Found', {
46 status: 404,
47 headers: { 'Content-Type': 'text/plain' }
48 });
49}
This script ensures that all requests to
images.soomal.ccare routed through Workers.By leveraging Workers' daily limit of 100,000 requests (3 million per month), it prevents excessive billing for R2 bucket access.
At this point, my goal is achieved. With 100,000 daily requests, this backup site has more than enough capacity. If the limit is exceeded, Workers will simply stop functioning, rendering the images inaccessible.
Add Additional Security Policies (Optional)
With the above settings, all requests to the R2 bucket must originate from soomal.cc.
This allows further security enhancements on the origin site to indirectly protect the images.
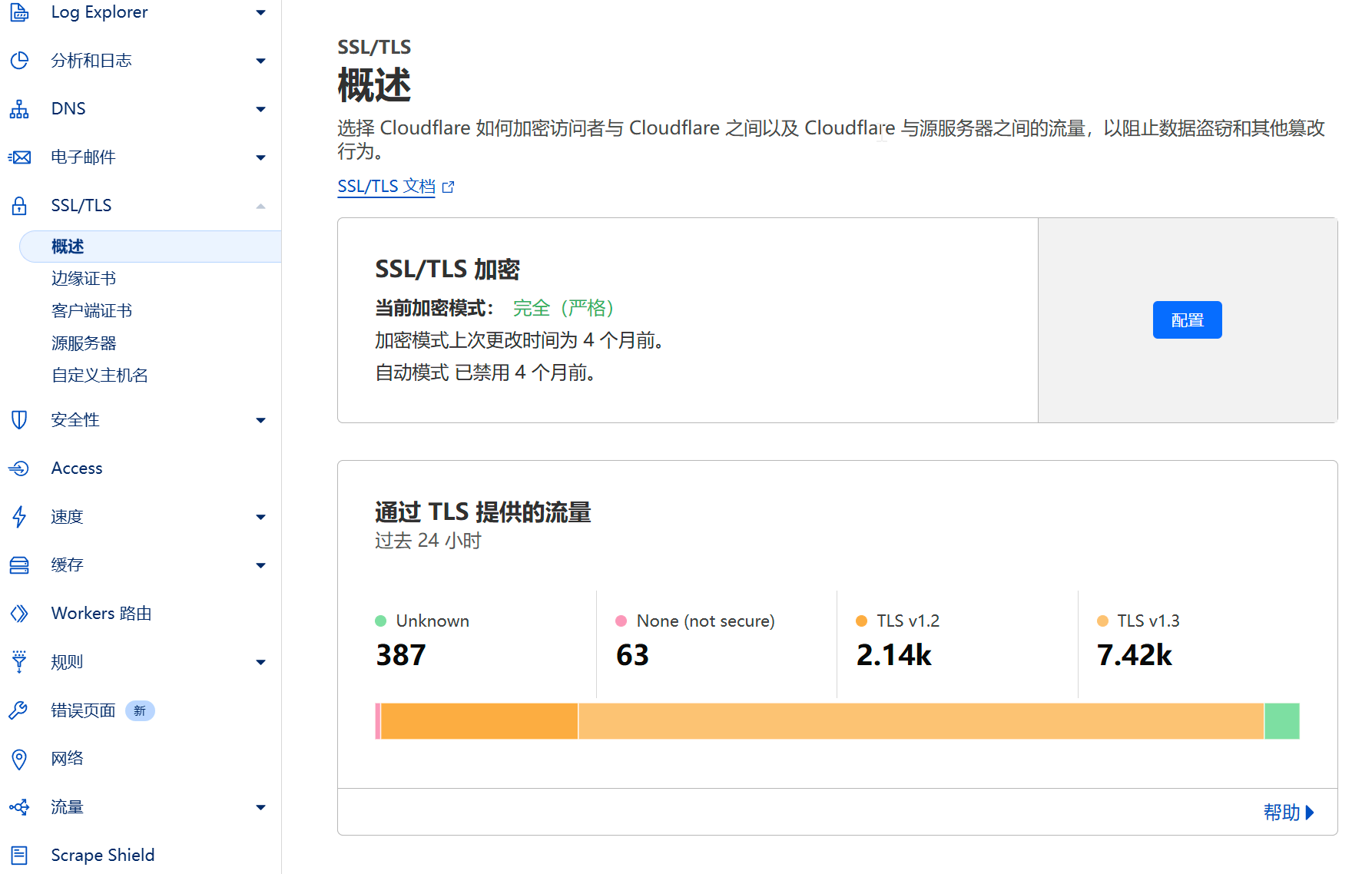
- Enable Strict SSL Mode.
- Enable Caching. Cache as much as possible.

- Security Rules. Enable features like continuous script monitoring, browser integrity checks, rate limiting, and bot attack mitigation for added protection.