Xiaomi Leaks User Accounts

Xiaomi User Account Leak Incident
Xiaomi Corporation recently leaked user data on a scale of tens of millions. The types of data that were publicly available for download are roughly as shown in the image below:
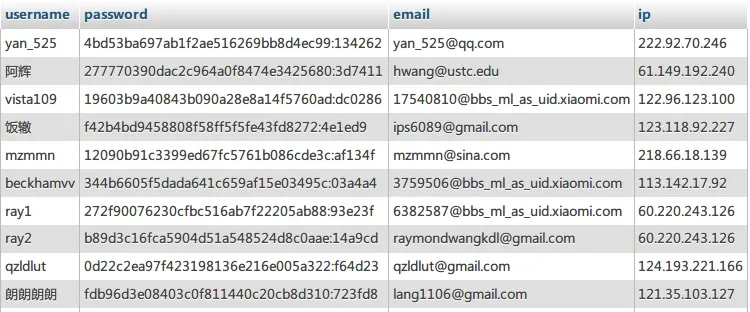
This batch of data includes usernames from the Xiaomi forum, passwords encrypted with MD5 salt, email addresses, and registration IPs. Currently, the usernames from the Xiaomi forum can no longer be used to log into Xiaomi services. However, the personal email accounts stored in the email field and the numeric prefixes of system-generated email accounts (i.e., the numeric IDs of Xiaomi users) can still be used to access Xiaomi services.
Since the passwords in the data package were encrypted using Discuz's built-in MD5 salt encryption algorithm, the password data in this package is not very meaningful to ordinary people. However, Discuz is a big target, and major cracking sites have long had corresponding methods to brute-force the MD5 salt encryption algorithm. It is said that the success rate of cracking this encryption method in a short time can reach over 70%, and about 90% of user passwords can be cracked within a few days. Therefore, this encryption algorithm is not too difficult for professional hackers; ordinary people can also purchase cracking services online to decrypt the passwords.
Xiaomi accounts are currently unified across all services provided by Xiaomi, meaning that the accounts used for data synchronization on most Xiaomi phones (or other Android phones with MIUI installed) are at significant risk. A Xiaomi account can not only view purchase records, addresses, and identity information on Xiaomi's website but also access synchronized data such as SMS, contacts, photos, and GPS information on the phone, and even provide remote locking and erasing functions for the phone. If hackers target users for one-on-one scams with malicious intent, the success rate would be extremely high.
Additionally, in the current internet environment, many users adopt a single security strategy, using the same username, account, and password across different online services. The result is often that once an account and password are leaked on platform A, other platforms also fall victim. In November 2011, after the leak of over 6 million user passwords from the CSDN forum, many users are still affected to this day. The two batches of accounts leaked by Xiaomi this time amount to 13 million, and it is conservatively estimated that at least 10 million account passwords will be successfully cracked by hackers. My Xiaomi account was unfortunately leaked in this incident, and to make matters worse, I have never purchased a Xiaomi phone but have used MIUI and Xiaomi's so-called cloud services on two Samsung phones.
Strengthening Account Protection to Reduce Cybersecurity Risks
In the current situation, cybersecurity mainly revolves around account security, which can be divided into four parts: username, password, password protection, and security email/phone.
1. Username
In most online application scenarios, usernames do not pose a significant security threat, as a username is just a lock, and the password is the key. Without the key, the lock itself does not pose a security threat. However, in certain specific situations, usernames can also pose a security risk, such as when the entire door needs to be protected.
Security issues like router access, website administrative permissions, virtual server permissions, and FTP permissions all require security measures starting from the username. To prevent hacker attacks, server path names, administrator accounts, FTP accounts, and other usernames should avoid using default names like admin, root, and administrator.
Cracking individual user passwords one by one is difficult, time-consuming, and inefficient, but cracking administrator accounts is much easier, especially those using default usernames. By continuously brute-forcing, hackers can gain various permissions within the entire server. For ordinary users, modifying router usernames is the most practical application.
Recommendations: Modify website administrator usernames, change website path names, alter FTP usernames, disable FTP anonymous login, and change router usernames.
2. Password
Everyone knows that passwords are the most critical aspect of cybersecurity, but passwords inherently have usability issues: they require manual memorization and single-character input. This creates significant obstacles for users, who often prefer simple passwords for ease of memory and input, rather than complex, hard-to-remember passwords, resulting in low overall cybersecurity levels.
Setting passwords is not easy. One memorable example is GoDaddy's backend FTP password requirements: 1) must include letters and numbers; 2) letters must include uppercase and lowercase; 3) must include special symbols like !@#%; 4) must not contain other special symbols; 5) password must be longer than 8 characters; 6) must not start with a number. After struggling to set such a password, a few days later, it's all forgotten.
In my opinion, the balance between password usability and security can be adjusted based on the type of online service.
- For entertainment and leisure websites, passwords should be easy to input, such as 000000.
- For daily-use services, passwords should be easy to input, slightly simplified, and follow a pattern. For example, QQ, WeChat, and Weibo could have passwords like qQ.10.24, wX_10_24, wB@10@24.
- For work email, security email, payment platforms, and online banking platforms, passwords must be at least 8 characters long, include special symbols, and follow a unique pattern. For example, Alipay, Bank of China, Google Mail, and QQ Mail could have passwords like bOc.10.24.vIp, gOO!gle!10!24!vIp, tEn@Cent@10@24@vIp, aliPay_10_24_vIp. This involves combining service passwords, using a staggered memory method, including personal-specific characters and numbers, and forming a pattern.
In summary, setting passwords is a long-term and challenging task. Individuals can create a set of rules only they can remember to generate strong passwords. I currently use family genealogy rankings to set different passwords. Normally, even if one password is leaked, it is extremely difficult for hackers to guess the others.
3. Password Protection
Password protection features are used on most platforms, providing a custom Q&A verification recovery function in addition to password and email/phone recovery. This feature is very susceptible to exploitation by hackers, especially by those with malicious intent close to the user.
Password protection questions are generally similar, mostly involving personal or family information. I recommend not filling in the answers truthfully when setting these questions. Given the severe state of personal information security, malicious individuals can often obtain user information through social engineering (many "hackers" themselves know a lot of personal information about the users they target), thus stealing passwords.
For example, for the question "Where was I born?", the answer could be a birth date, a favorite saying, or a pet's name.
Of course, the most severe issue with password protection questions is that users often cannot remember what answers they set. To address this, it's best to establish a fixed pattern or even write it down to simplify memory. The purpose of password protection questions is to ensure password security, not usability, so unique answers are crucial.
4. Security Email/Phone
Ultimately, cybersecurity relies on email or phone as the last line of defense. This means that almost all network account security features are fundamentally designed based on email and phone numbers. Once an email password is leaked or a phone is used by someone else, all security settings become ineffective.
Email security settings can refer to the above three steps; phone security is another broad field.
There are two principles for using a security email:
- Never use the same password for your email as for other accounts! Once one platform's password is lost, other platforms may be attacked. For example, the Xiaomi account leak could lead to the leakage of email account passwords for at least millions of users (assuming most email users use the same password for their Xiaomi accounts).
- Do not direct all network services to the same security email unless you are absolutely confident in its security. Don't put all your eggs in one basket. Even for emails, account A should use account B as a backup security email. If email B is compromised, all services secured by email A are at risk.
As for phone security, as long as the phone is not lost, and you avoid installing software from unknown sources, using ROM systems from unknown sources, and install appropriate security software to remove viruses and malware, it is generally difficult to be hacked. If the phone is lost, immediate measures like reporting the loss and replacing the SIM card are essential.
Summary:
Cybersecurity requires sufficient attention. Personal behavior is predictable, and in many scenarios, individual users tend to use the same username and password over a long period, with the same password being reused across multiple platforms. Unfortunately, the behavior of network hackers is unpredictable. Even user data leaked many years ago is still being parsed by hackers. Different hackers can use the same batch of data for different purposes—some for fraud, some for theft, and some purely for destruction. To guard against these unpredictable risks, proper management of accounts and passwords is extremely necessary.
#passwords #xiaomi #cybersecurity #internet